- Become a Lawyer
- Become a Principal
- Visiting Lawyers
- Membership Services
- How to Become a Member in Alberta
- Billing Cycles, Filing Deadlines and Other Key Dates
- Status Options & Contact Information Changes
- Making a Payment to the Law Society
- Membership & Indemnity Program Renewals
- Member & Indemnity Certificates
- Indemnity & Indemnity Exemptions
- Professional Corporations (PCs)
- Limited Liability Partnerships (LLPs)
- Complaints
- Alberta Lawyers Indemnity Association (ALIA)
- Western Canada Competency Profile
- Continuing Professional Development
- Practice Advisors
- Trust Accounting & Safety
- Practice Management Consultations
- Equity Ombudsperson
- Fraud & Loss Prevention
- Approved Legal Services Providers
- Forms & Certificates
- Home
- Lawyers & Students
- Alberta Lawyers Indemnity Association (ALIA)
- Universal Cyber Coverage Program
- Cyber Hygiene Best Practices
Cyber Hygiene Best Practices
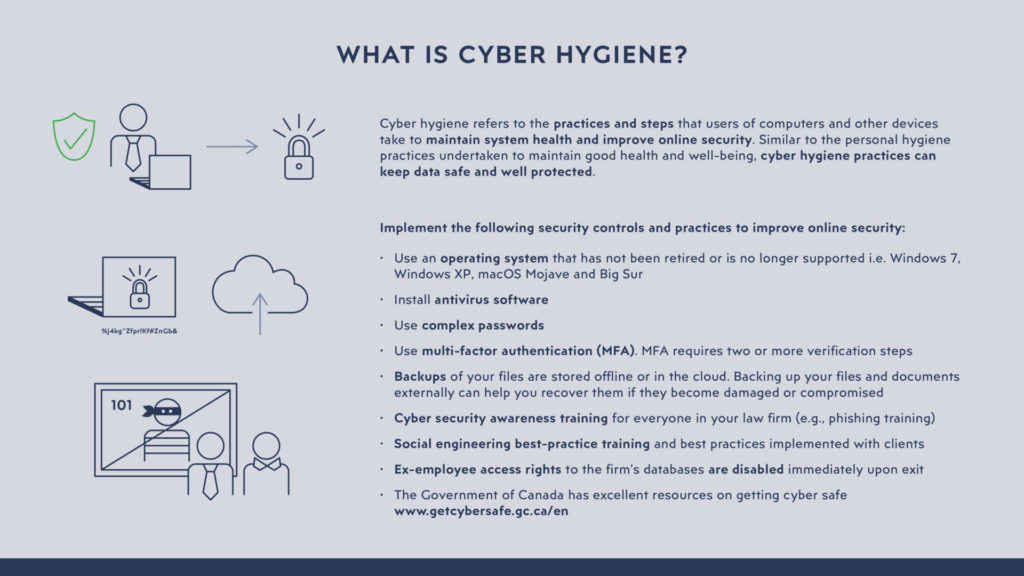
Cyber hygiene refers to the practices and steps that users of computers and other devices take to maintain system health and improve online security. Similar to the personal hygiene practices undertaken to maintain good health and well-being, cyber hygiene practices can keep data safe and well protected.
General security tips
- Do not use an operating system that has been retired or is no longer supported, i.e., Windows 7, Windows XP or macOS Mojave and Big Sur.
- Regularly update the operating system and other software/applications you use. This will ensure you have the latest security associated with these programs.
- Install antivirus software.
- Use complex passwords, including upper case, lower case and special characters and numbers, and change them regularly. Click here to view the Government of Canada website on passwords.
- Click here to read Law Society of Alberta’s resource on password managers.
- Incorporate multi-factor authentication (“MFA”) into your systems. This helps prevent ransomware attacks and other cyber threats. MFA requires two or more verification steps, such as a password and a secondary code received via email or text messaging, to access your devices or accounts. For example, you would use a password and a secondary number code from an app on your phone. Click here to view the Government of Canada website on multi-factor authentication.
- Back up your data regularly and store it offline or on the cloud. This will allow you to restore from your backups without losing too many days of work in the event of a cyberattack.
- Conduct cyber security awareness training for everyone in your law firm (e.g., phishing training).
- Conduct social engineering best-practice training and implement best practices with clients.
- Disable ex-employee access rights to the firm’s databases immediately upon exit.
The Government of Canada has excellent resources on getting cyber safe.
Employee awareness and cyber hygiene
- Have all employees take cyber security awareness training annually (i.e., phishing training). Educate employees and end users on how to spot phishing emails and recognize the red flags to reduce clicks on malicious emails. Many ransomware attackers use scams like phishing to gain a foothold in a network. Click here to access the Government of Canada website on ‘Get Cyber Safe’, which includes information on phishing and the seven red flags of phishing.
- Always secure laptops and confidential documents—do not leave them in cars or unattended and unsecured overnight in the office.
- Limit access to confidential information to key people. Make sure secure areas really are “secure” and locked.
- If an employee is to be terminated, plan in advance to block the employee’s access to prevent any deletion, alteration or theft of confidential information.
Common ways to spot and prevent phishing emails and scams
- Spelling and grammar mistakes within an email.
- Minimal or vague details provided about the request.
- Requests for money or financial information (including an unusual or unexpected invoice or a wire transfer to a foreign country).
- A link within an email that prompts your login credentials.
- An unusual urgency or time-sensitive nature to the request.
- A stated or implied need for secrecy (such as an instruction not to call them over the phone).
- An unexpected request from a vendor or client to change their banking or payment information.
- A sender’s email address that is external or contains misspellings.
How to deal with suspected phishing attempts
If you receive a suspicious email from someone you know, call or speak to the sender in person to verify that they did, in fact, send the message. If you cannot verify that the sender actually sent the message, or if the person who allegedly sent the message informs you that they did not send it, alert IT personnel or another appropriate resource immediately.
